Update: This guide covers using OPNSense’s native Policy based Rule management, you can also use ‘suricata-update‘ to do similar, if not more, focused/tailored Rule management. If you are interested, please see our post about enabling the modification here Using Suricata-Update on OPNSense
OPNSense is an Open Source FreeBSD router, firewall, and has a modern Suricata 6 (update: now 7) to go along with it. This guide is a how-to in getting additional insight and ability to respond to network events.
The default rules are good, but, if there is a strong interest in network events, and possibly want to be more aware of the ins and outs of the network, more rules are better. To get to this end, it is suggested to to follow the steps outlined below. This guide does not touch adding custom rule sets, that will hopefully be in a future guide – but others have made guides to this affect and Google search should get you there.
Some of the choices shown are more of a preference. There might be a desire to enable all the rules, if so, the last Policy definition detailed might not have to go into the explored roll-out, plus, the list of ‘noisy/trouble-some’ SIDs might not need to be set. TLS/SNI/DNS connection/resolution rules are IMHO generally not fun to store/filter/etc. if they have approaching-zero impact, so it is recommend to follow the whole roll-out.
Requirements to start
- Working OPNSense router
- Interfaces configured for Suricata/IDS to watch
- The ability to log in to admin/root
- The ability for the router to reach the internet is assumed
Enable additional Suricata/IDS rules
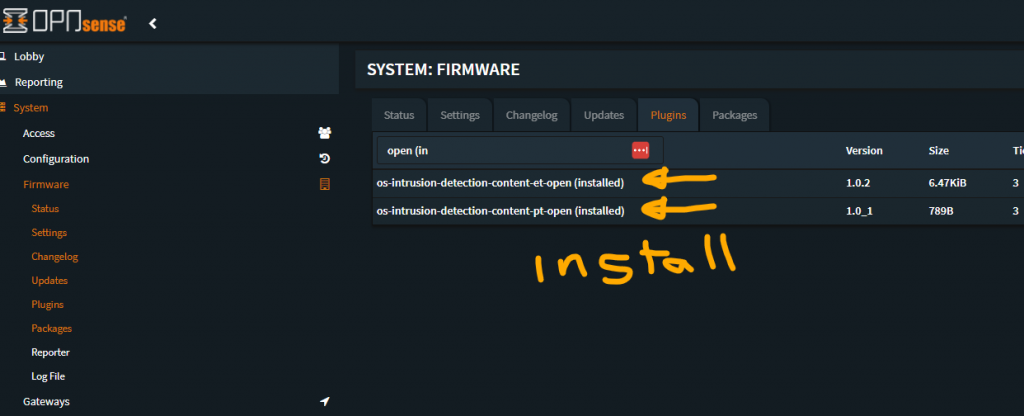
Navigate to “System -> Firmware -> Plugins” and install the two intrusion detection open plugins
- os-intrusion-detection-content-et-open
- os-intrusion-detection-content-pt-open
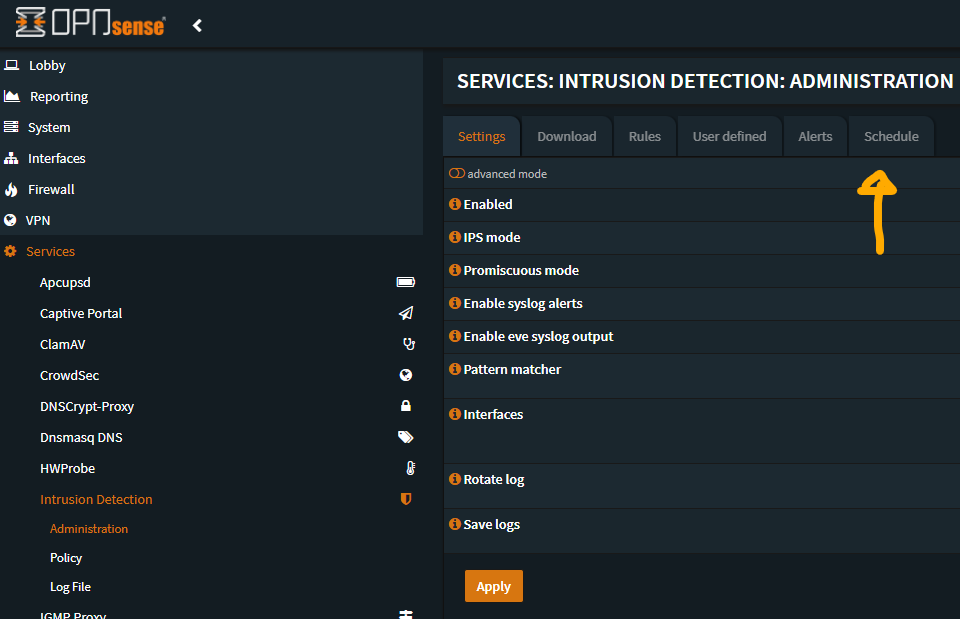
Set a CRON Job to sync these rules
Navigate to “Services -> Intrusion Detection -> Administration” and click on “Schedule”
What will be presented is a Cron Editor, one could navigate to this menu space (there are are quite a few good things one can schedule here) and manually select the command “Update and reload intrusion…”, this navigation method/menu-start, does it automatically
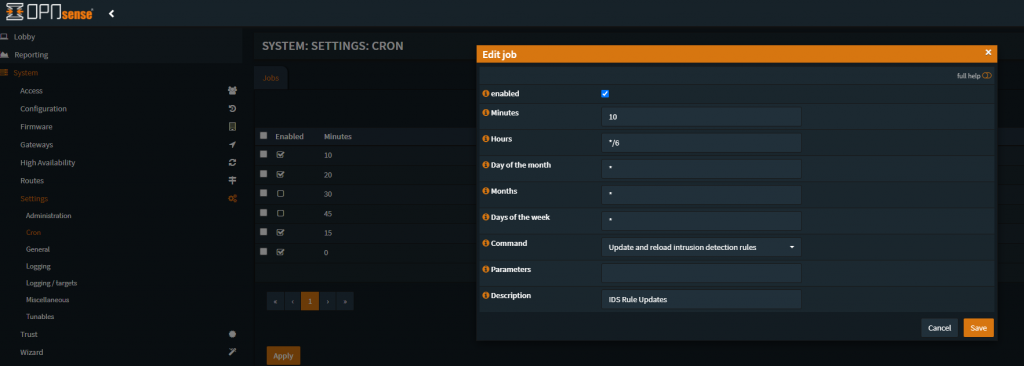
After setting the settings for the schedule, Hit “Save” in the lower right of the menu
Enable IDS Rules via OPNSense’s Policy Settings
Navigate to “Services -> Intrusion Detection -> Policies” and click the “+” (plus) mark on the initial lower right of the menu
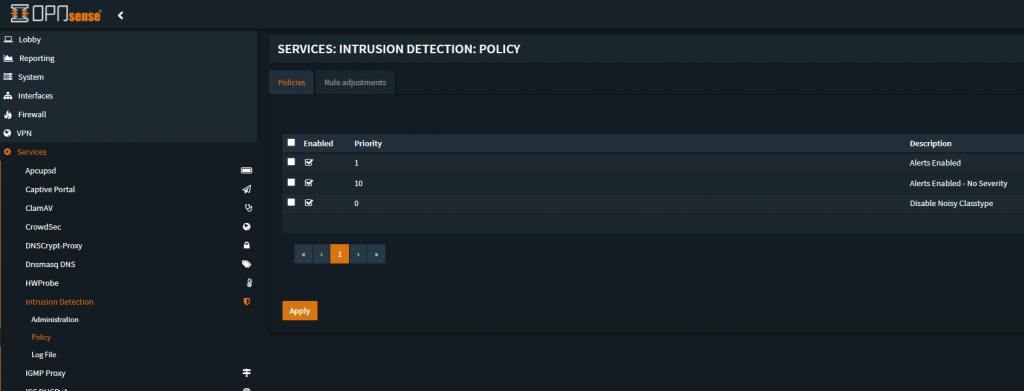
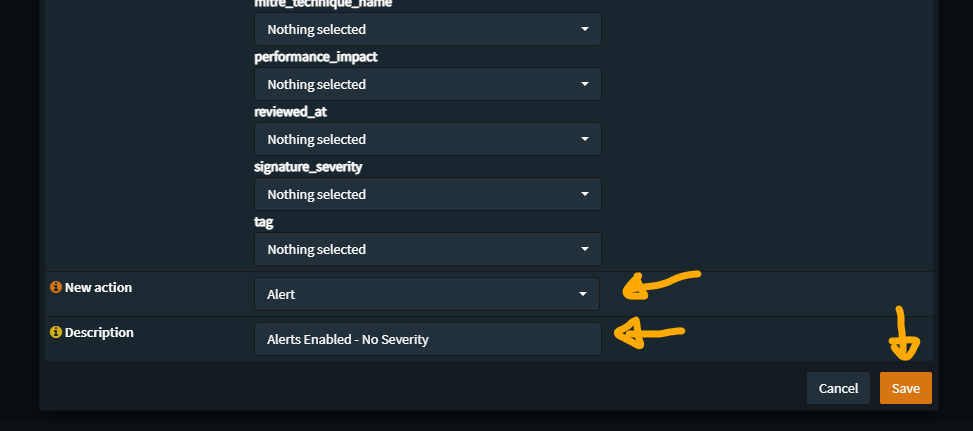
What will be presented is a Policy add menu, and we will be making three policies, the first two enable (possibly) all the rules in the rule sets installed, the third disables most of problematic/noisy/DNS resolution based activity alerts
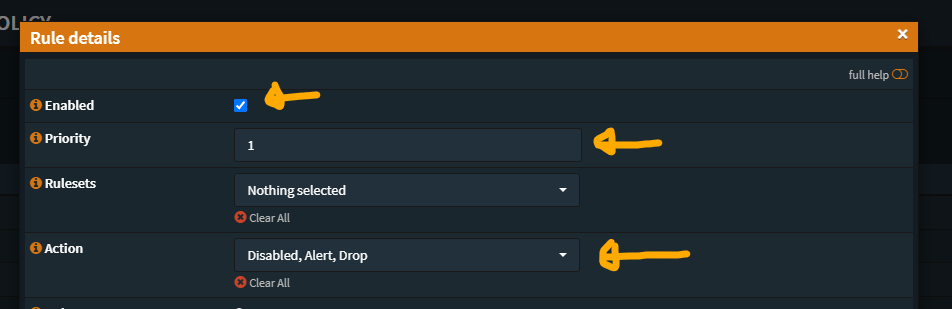
The first Policy enables most of the SID Rules
This policy is pretty clean, there are four primary “signature_severity” elements, I don’t see this changing anytime soon, so this Policy should keep things in line with no expected changes so far
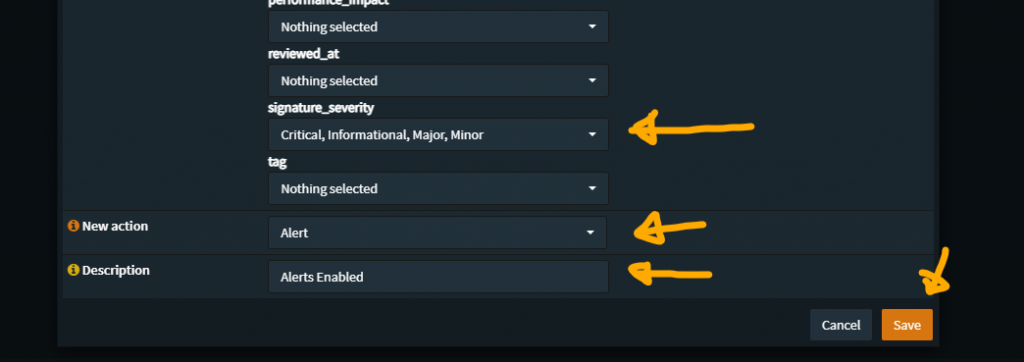
The second Policy enables ‘the rest’ of the SID Rules
As far as making sure I really “get all enabled”, there’s a chance I’m still missing a few, but it is unlikely
Over time it may become necessary to revisit this Policy to enable new “classtype” elements that show up – there is no select all here, there will be a need to be clicking each item in the list, which works well enough here
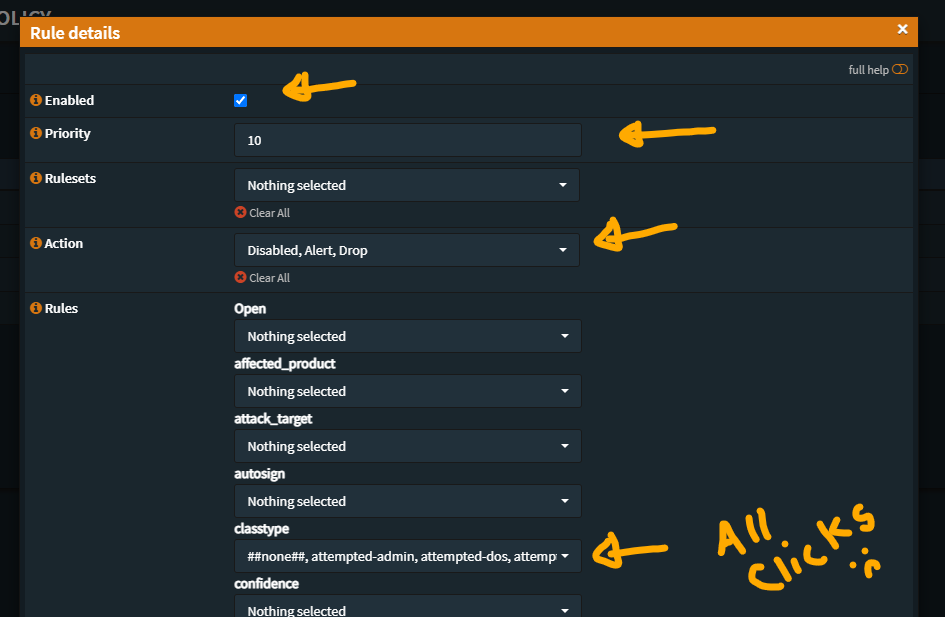
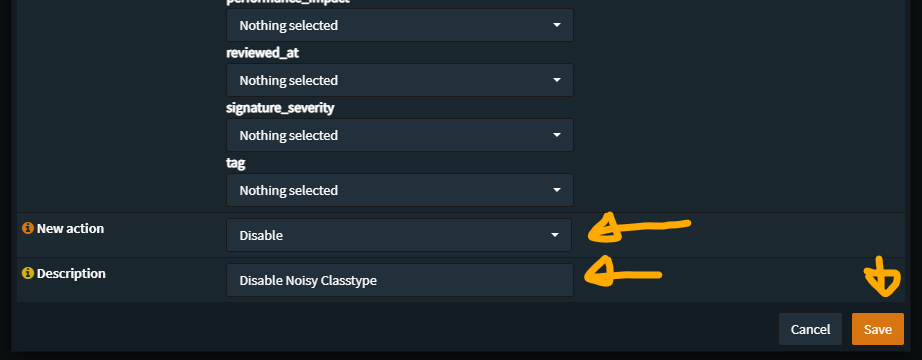
The third Policy disables the noisy/troublesome SIDs
Here we will be selecting what the items we do not want to see, this is where personal preferences comes into play, but in strong recommendation, disable these as they are SNI/DNS/TLS based and generate an event with every resolution – which will fill up disk/event storage rather quickly and be a bother to sort/filter through
Recommended selection items:
coin-mining
file-transfer
mail
media-streaming
messaging
misc-activity
not-suspicious
policy-violation
social-media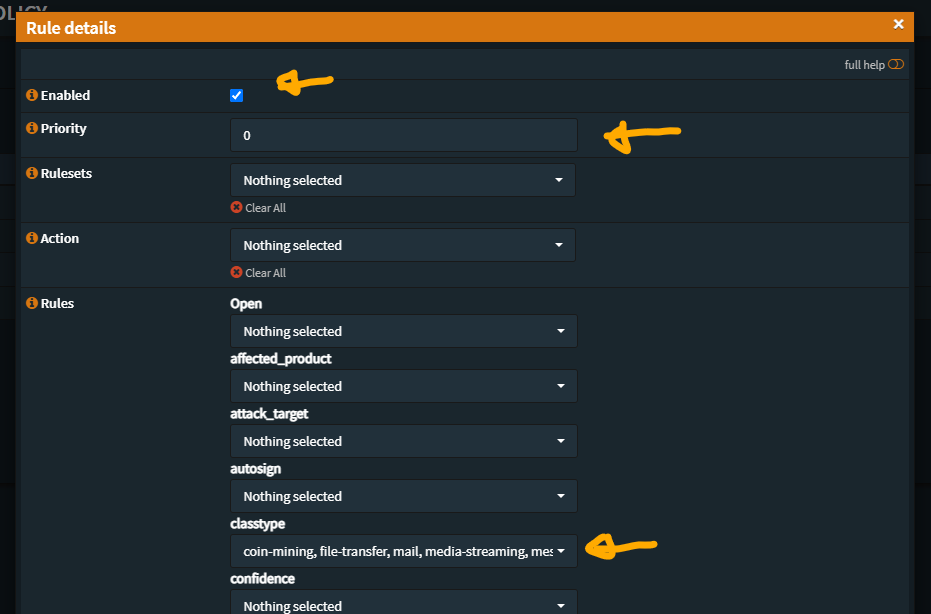
Now we have three Policies enabling and disabling a ‘mask’ if you will, of the rule sets. This still enables just a few bothersome SIDs that will require manual tuning
In the future it is a hope to approach this with Suricata-Update or Python scripting, possibly API use, but, as it is OPNSense’s GUI and method here is quite fast and approachable and allows one to handle the needful here
Once greater horizons are explored, the hope is to work out some of the ANY to EXTERNAL/HOME rule updates and more
Disable a select few bothersome SID rules that will now be enabled
Navigate to “Services -> Intrusion Detection -> Administration” and click on the “Rules” Tab
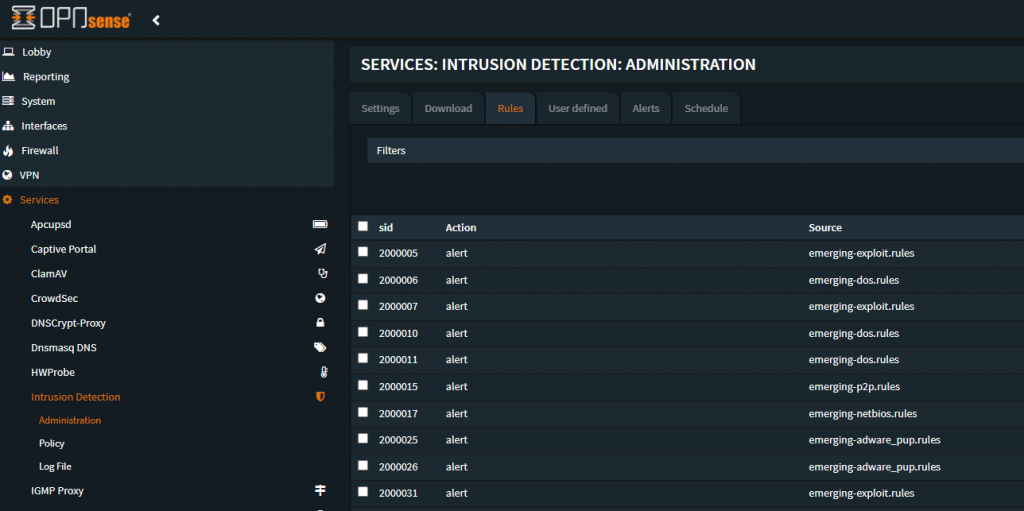
Use the list below, one can enter the SID in the search box on the upper-middle right, and when you see the SID in the list, click the check mark on the left of that SID – thereby disabling each SID specifically
Hit the “Apply” button at the bottom once the changes have been completed
This overall method allows Policy to affect many at once, and for less than ~50 custom mods, edit individually
This approach is what OPNSense will strongly suggest if one tries to make many rules at once, or possibly if the population gets too large
List of SIDs to disable individually:
2012647
2021076
2030387
2100485
2100486
2100408
2002752
2009701
2009207
2009205
2009206
2009208
2011803
2008470
2102329
2028371
2027759
2027865
2027757
2012510
2101852
2100648
2036752
2009080
2103132
2103133
2103134
2101390
2100650Thanks for reading, please comment with any experiences, the hope is to keep this guide up to date as OPNSense matures and link to a future API/Python/Suricata-Update style follow-up or full conversion of what this roll-out sets for state